JADC2 Comms Convergence and RoIP Access at the Tactical Edge

Customer
Joint Staff and Pentagon Joint Warfighting Concept (JWC)
U.S. Air Force Advanced Battle Management System (ABMS)
U.S. Army Futures Command Project Convergence
U.S. Navy Project Overmatch

Application
The goal of the Joint All-Domain Command and Control (JADC2) effort is to connect military assets across space, air, land, sea, and cyber domains to enhance command and control capabilities. This will enable the United States to "sense, make sense, and act" faster than its adversaries. Success depends on speed—requiring more data from diverse sources and real-time data interpretation using cutting-edge technologies like Artificial Intelligence and Machine Learning.
Challenges
&
Solutions
The challenge requirements are listed in blue; ASTi's applicable components are

Ease of Use
JADC2's complexity requires a modular design that focuses on ease of use for operators and system administrators alike. While some training may be necessary, it should be minimized. Adding features to the solution should consider existing user knowledge and deployment conditions to ease integration.
Operators use ASTi's intuitive Flex Client that provides a single pane of glass, customizes by mission, and requires minimal training. System administrators access a web interface to review comms settings, complete with built-in help menus and other features that explain capabilities and functionality.
Quick-restore procedures and profile sharing between systems facilitate knowledge transfer and growth within the JADC2 ecosystem. This maximizes reuse and organically develops optimal user setups. Feedback from demonstrations, experiments, and rapid prototyping is incorporated into the fielded product within days or weeks. ASTi takes an iterative approach to ease of use, ensuring solutions are based on real-world data rather than theoretical guesswork.
End-User Devices (EUDs)
Mission-critical access requires connectivity from any device on any network at any time. Such devices could include ASTi-provided interfaces like the Flex Client on rugged tablets, laptops, or smartphones, as well as hardware-only PTT clients without GUIs. Alternatively, third-party MANET-compatible PTT devices and OEM RF radio hardware as endpoints must also integrate with the proper comms solution, since ASTi cannot provide all devices for every situation.
ASTi EUDs like the fully configurable Flex Client can be tailored to individual roles and user needs, whether simple or complex. When users prefer existing applications such as Android Tactical Assault Kit (ATAK) or Solipsys Battlespace Command and Control Center (BC3), our Open API architecture provides seamless integration without requiring users to leave their preferred application.

Modular Open Systems Approach (MOSA)
Seamless Multi-Domain Operations (MDO) are only possible when the various military systems communicate and operate as one rather than isolated platforms.
ASTi builds this into our products from the outset, emphasizing interoperability, integration, open standards support, and modularity. Voisus and Comms Logger software can run on bare-metal, be virtualized, or containerized based on customer requirements. Hardware support comes from multiple sources, including ASTi OEM and program-specific solutions or existing commercial solutions from companies like KLAS Voyager or Curtiss-Wright Pacstar. Within these solutions, Voisus and Comms Logger use open standards, support secure APIs, and maintain compatibility with both current and legacy radio and telecom equipment.
Seamless Interoperability, Access and Security Levels
Tactical Edge communications for DOD agencies and allies requires hybrid solutions combining legacy and current technology, RF waveforms, voice CODECs, messaging and network protocols, security classification levels, and OEM equipment. The need to support diverse data types and communications standards while achieving effective joint and coalition interoperability makes seamless integration, access, and security levels critical.
Voisus RoIP beyond-line-of-sight (BLOS) access, cross-banding, and CODEC transcoding support all required waveforms (e.g., MANET, UHF, VHF, HF, SATCOM, Link-16, etc.) and CODECs. Radio Security Level Key Tagging within the Flex Client enables manual or automated CIP key tagging (secure versus unsecure) when Remote Control command and control (C2) interface is active. This Information Assurance (IA) cross-mute logic prevents cross-keying of radios, intercoms, and VoIP calls with mismatched security keys. Multiple communications routing techniques are supported to use the best option for current Tactical Edge situations. These include full stand-alone kit, direct one-to-one or one-to-many capability, and centralized cloud-based hub that aggregates and distributes audio and data to all network kits when cloud access is available.
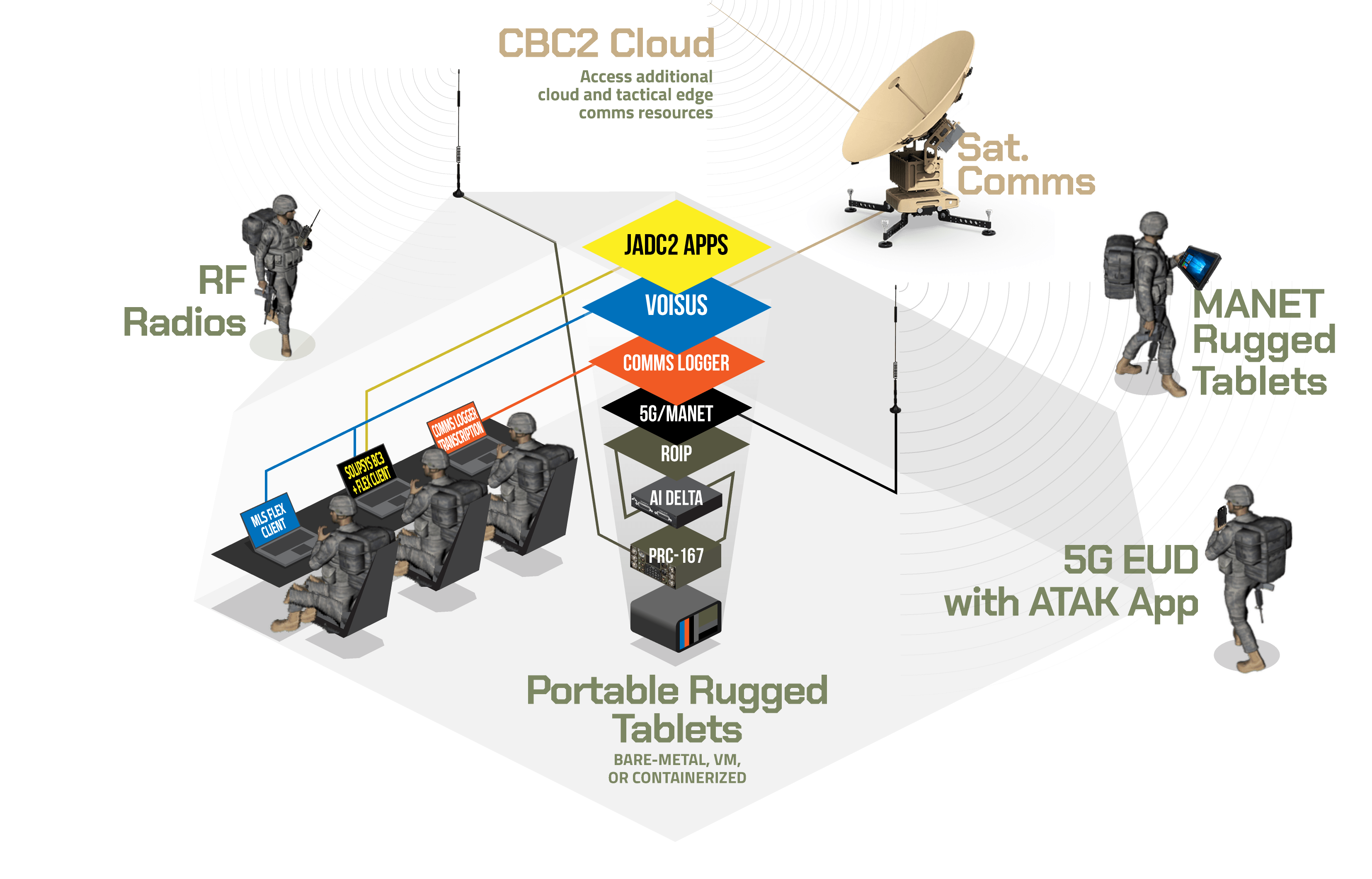
Deployed at the Tactical Edge, but Cloud Accessible
Reduced hardware footprint and low size-weight-and-power (SWaP) ruggedized kits must be part of an agile, scalable, and survivable solution for rapid deployment. The kits must adapt to evolving requirements, integrate with C2 comms, and support future growth including: integration with sensor grids, cloud-based C2 apps, and AI/machine learning software. When available, cloud-based-C2 (CBC2) pipelines and infrastructure must be used. Under Denied, Disrupted, Intermittent, and Limited (DDIL) field conditions, however, the kit must perform to maximum capability while enabling subsequent synchronization between Deployable Digital Infrastructure (DDI) nodes or kits and CBC2.
ASTi's RoIP and Remote Control module provides tailored support for BLOS remote control under harsh DDIL conditions. The Flex Client uses a layered comms approach, ensuring that if one link is compromised, other available links can still be used.
Agentic AI Interface Support
The DoD requires an AI-enabled force because speed will decide the outcome of future battles. This includes speed to understand the battlespace, determine the best course of action in complex and dynamic environments, and take those actions. Together, these capabilities enable faster execution of the OODA Loop (Observe, Orient, Decide, Act).
The Voisus TOC-L Communications server was the first JADC2-enabled comms solution to connect with an external agentic AI system. The Voisus interface enabled the agentic AI to communicate with live tactical systems. Voice comms between human EUD operators and AI agents remained highly effective despite operating in noisy RF environments under unpredictable conditions.
Comms Logging and Bespoke C2 Transcription
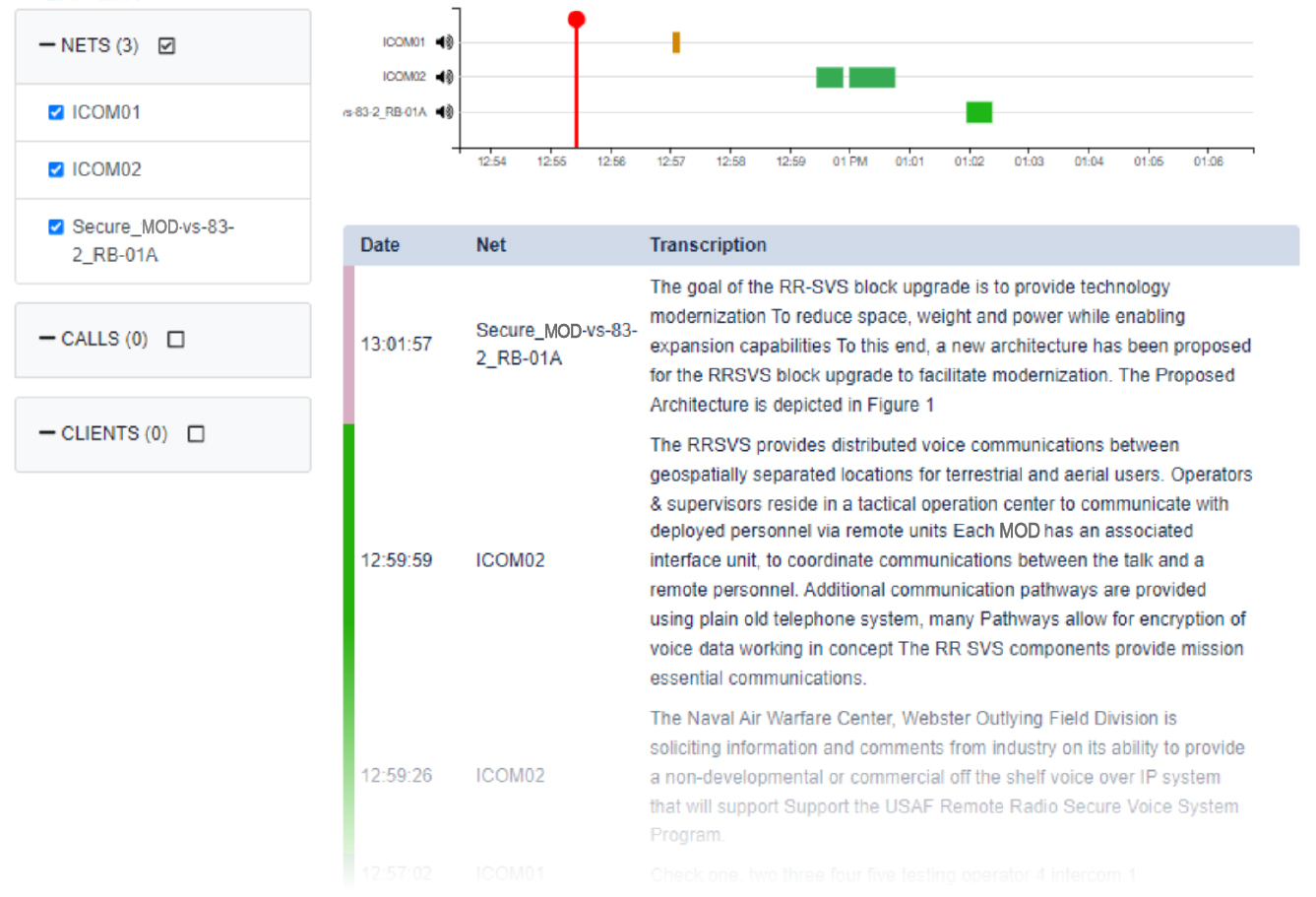
Accurate capture and retention of communications is essential for maintaining situational awareness, conducting after-action review, and ensuring accountability in dynamic decision-making environments. Automatic transcription quickly converts voice comms into searchable text for immediate integration into common operational pictures and network sharing. This enables faster information dissemination, supports real-time decision-making, facilitates multi-language coalition operations, and allows automatic analysis for keywords, threats, and operational patterns.
ASTi's Comms Logger provides a time-stamped and graphical representation of stored voice communications grouped by networks, radios, EUDs, and clients. It captures comms at the Tactical Edge under DDIL conditions or via cloud when connectivity allows. Voice-to-text transcription focuses on semantic JADC2 recognition rather than general speech patterns, ensuring accuracy and contextual relevance. Audio and transcriptions can be exported in industry-standard formats or translated to and from English.

Software Maintenance and Cybersecurity Accreditations
JADC2 Information Assurance at the tactical edge requires a comprehensive security framework that combines zero trust architecture, cross-domain solutions, robust identity management, and resilient communications. This framework must protect data flows across multiple classification levels while enabling real-time decision-making in contested environments.
ASTi maintains a proven, long-term commitment to safeguarding protected information through a complete spectrum of security and IA solutions. All of our products are built on a solid security foundation and meet government accreditation standards including ATO, ATC, IATT, FISMA, and FIPS. Since 2005, ASTi products have continuously held U.S. Government IA accreditations through various security initiatives, including the current Risk Management Framework.
Systems can be updated locally or remotely via cloud, SATCOM, 5G, or RF regardless of their location. With proven compatibility with COTS and GOTS cross-domain solutions, zero-trust components and principles, and latest TACLANE and CSfC options, ASTi products can be used in almost any secure configuration required by today's missions.
Rapid Prototyping
Rapid prototyping requires delivering operational capabilities within compressed timelines, emphasizing iterative development, open architectures, and agile methodologies to accelerate ongoing development while maintaining interoperability across domains and classification levels. Since JADC2's inception around 2020, it has evolved rapidly, requiring comms solutions to continuously adapt.
Many features in the current ASTi solution were added based solely on warfighter feedback. In 2024 alone, our TOC-L Communications solution participated in over a dozen mature prototype demonstrations and experiments, including Project Convergence Capstone (PCC5), Valiant Shield, and ShOC Capstone. ASTi integrated with an agentic AI system within two weeks of the warfighter request. Local testing and customer systems integration labs (SILs) support continuous prototyping efforts. As a small company with more than 35 years of experience, ASTi's core strength is its agility and ability to meet changing customer demands. We were agile before DevSecOps and Scrums became popular.